How do you write an enigma code? The encryption code returns an element from the alphabet array The Caesar cipher is probably one of the most basic ciphers, although it was the basis of the Enigma codeSYMBOLS CIPHERS CODES CRYPTO CHARTS GRAPHS See more ideas about ciphers and codes, charts and graphs, symbols
1
What is enigma code
What is enigma code-A Caesar Cipher is a special kind of cryptogram, in which each letter is simply shifted a number of positions in the alphabet It can easily be solved with the Caesar Cipher Tool A ROT13 Cipher is similar to a Caesar Cipher, but with a fixed shift of 13 letters It can easily be solved with the ROT13 Tool Sample CryptogramThe Enigma machine was created for Germany by Arthur Scherbius in World War IIt is a cypher machine a way of changing the letters of a message so that it appears to be scrambled letters (or, random letters) Each time a letter is typed, it appears as another letter in the alphabet The choices are not randomThey are decided by a series of rotors which are set each day to a



Http Www Singingbanana Com Enigmaproject Maths Pdf
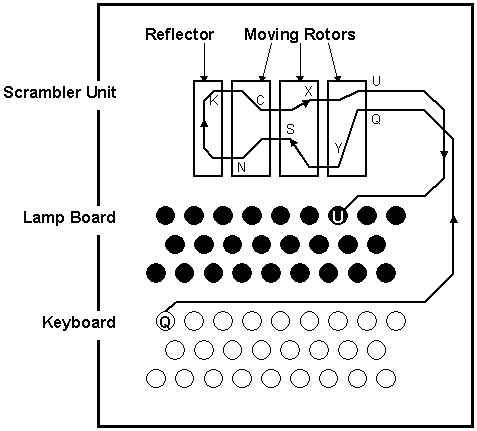
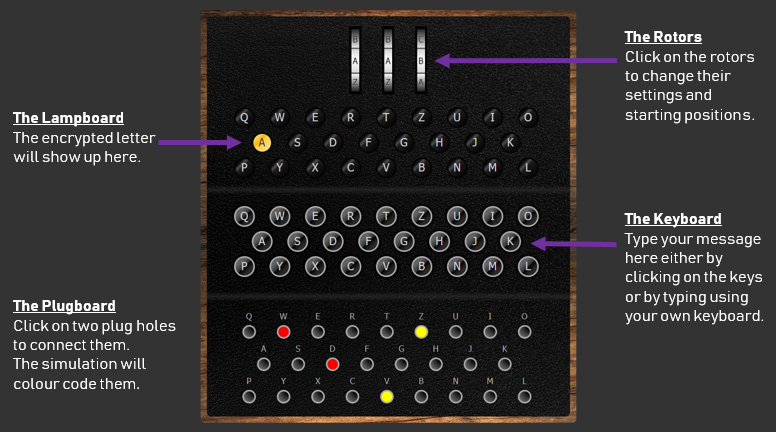
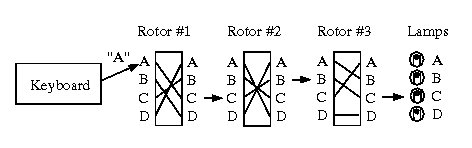
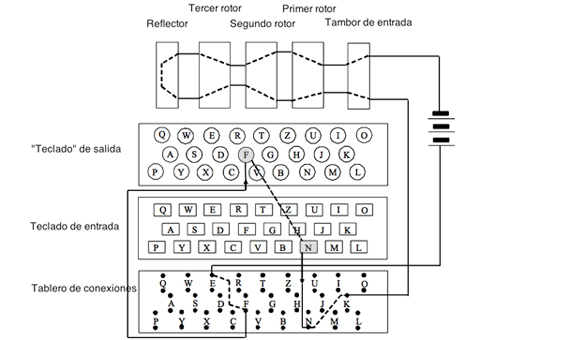
Simplified Enigma machine that is limited to a six letter alphabet Figure 4 Simplified version of a Enigma machine with one rotor The disk on the left is the keyboard, the middle ring is the rotor, and the disk on the right is the lampboard The wiring of the rotor determines how the plaintext letters will be encrypted The three rotors in the Enigma machineSourceWikipedia The military Enigma Machine had another set of encryption layers by using switchboards where each alphabet got mapped to another alphabetEnigma's Secrets How it Worked and How the Code was Broken By way of introduction, see the Historical Background to Enigma and the Key Players Involved The Working Principle The Enigma machine basically provided a simple substitution of a plaintext symbol with a different ciphertext symbol generated by the machine What made the machine special however was that
What Made the Enigma Code Special?Answers for Enigma Coded Messages CRACKING THE ALPHABET CODE The following page (entitled "Secret code for missing items") needs to be decoded On the inside back cover are flaps that open to a codebreaking system Readers are told that to crack the code they need to turn the three dials to show the correct symbolsConverts alphabet characters into their corresponding alphabet order number (eg A=1, B=2, , Z=26) while nonalphabet characters are being dropped Text to octal Hex to Ascii85 Integer encoder Enigma machine Text to base64
An Enigma machine is a famous encryption machine used by the Germans during WWII to transmit coded messages An Enigma machine allows for billions and billions of ways to encode a message, making it incredibly difficult for other nations to crack German codes during the war — for a time the code seemed unbreakable Alan Turing and other researchers exploited aEnigma The web app (and the excel sheet below) is a historically accurate simulation of the M3 Enigma code machine as used in World War 2 Rotors 1,2,3,4,5 are wired as they were in the original machine Rotors 6,7,8,9,10 are new rotors which can be rewired in any way you like, provided a genuine permutation of the alphabet is chosen The enigma machine was used in World War II to encrypt secret messages The Enigma machines are a series of electromechanical rotor cipher machines The first machines were invented at the end of World War I by German engineer Arthur Scherbius and were mainly used to protect commercial, diplomatic and military communication Enigma machines became




Pin On Clues Games Escape Rooms



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher
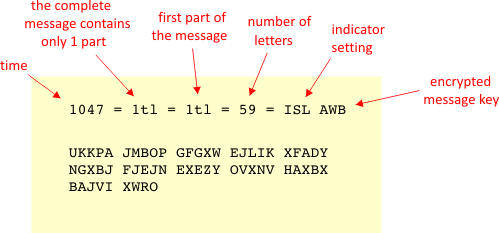
To encrypt your message with an Enigma machine, you would simply type a letter andwrite down which corresponding letter lit up on the alphabet For each key press, the rotors would move and the message was treated as one, so you had to send the full beginningtoend message to your recipientEnigma Cipher complete the lab by implementing the Engima cipher Note The code for the Engima cipher is more complex than the rest of this labI recommend implementing your lab assignment in 4 phases Review and understand the Cipher and Caesar classes;




In This Lesson We Will Understand Ppt Download




It S A Cipher For Fez Ciphers And Codes Alphabet Letters
In wigwag code, messages were spelled out according to a letternumber code Each letter of the alphabet was represented by a combination of numbers, and the numbers corresponded to flag movement A movement to the left of the center meant a "1," and a movement to the right of center meant a "2" The Enigma code, a veryThe Backwards Alphabet Code is very simple All you have to do is make a list of all the letters in the alphabet, and then make another list right next to it, of all the letters in backwards order Kind of like this A = Z B = Y C = X D = Wand so on, through the alphabetComplete implementation of a menubased interface Complete implementation of the Rotation and Substitution ciphers;



Web Stanford Edu Class Cs106j Assignments Assignment 05 Cryptography Pdf



Enigma Codeproject
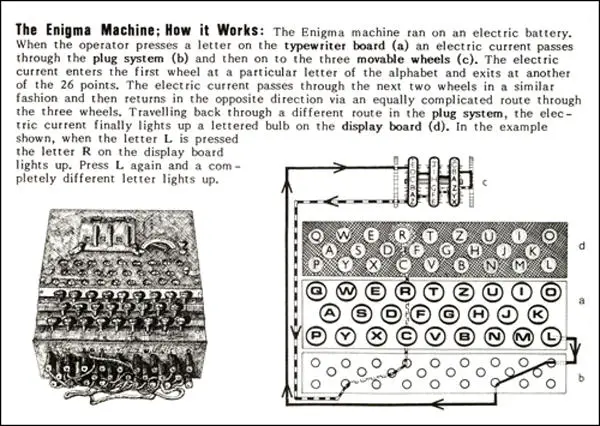
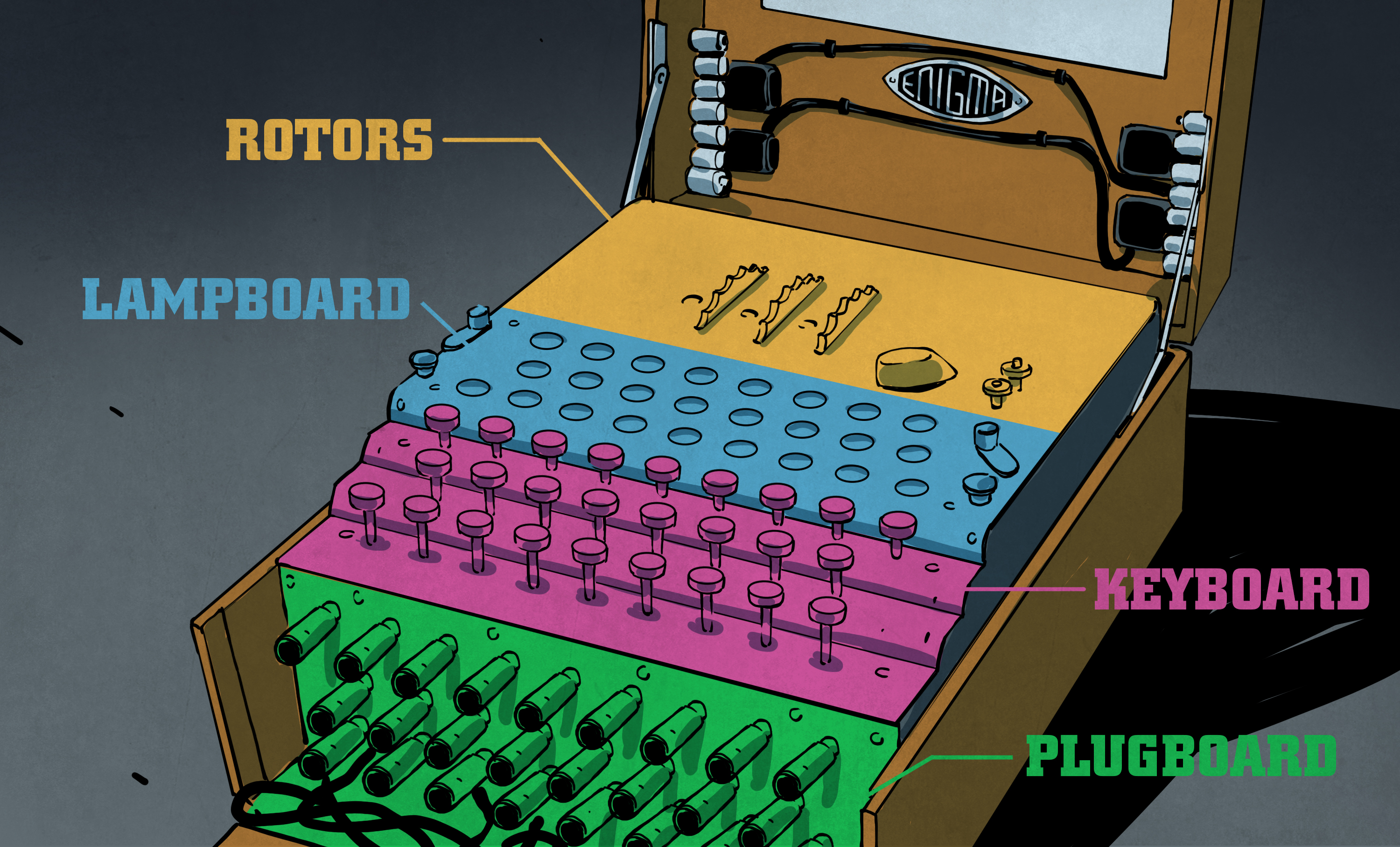
One would wonder why the encryption mattered anyway, and why it took a lot of effort to decode it The quality of codes is determined by the number of possibilities of getting the correct answer In the case of the Enigma code, one had to get all settings on the Enigma machine right before you could decode itAbout the size of a breadbox and containing a lampboard, a typewriter keyboard, and a plug board for electric cables, the heart of the Enigma system was a series of rotors (usually three or four) containing the alphabet Using a prearranged code system in a codebook, code combinations for Enigma machine typed messages ran into the tens of millions The enigma rotors The rotors are special gears with 26 pins Every pin is related to an English letter When an electric signal (in mechanical machine) comes to



The Enigma Machine And The Ultra Secret South African Military History Society




The Enigma Enigma How The Enigma Machine Worked Hackaday
Figure 4 details of an Enigma rotor (1) The finger notches used to turn the rotors to a start position (2) The alphabet RING or tyre round the circumference of the rotor (see below for an explanation of its significance) (3) The shaft upon which the rotors turn (4) The catch which locks the alphabet ring to the core (5) (5) The CORE containing the crosswiring between contactsAlphabet, let's take another look into the Enigma machine The Enigma as Matrices The Enigma is not a monoalphabetic cipher, but a polyalphabetic cipher This is a result of the rotor movements mentioned above Imagine a linear function E maps R26 to R26, although The Enigma of Code Talkers the dawn of the written language In fact, one of the earliest recorded uses of a machine ago The Caesarcipher shifts the alphabet forward three places to create a new alphabet for sending secret messages When we think of secret codes, however, the images conjured up




10 Codes And Ciphers Commonly Used In History Coding For Kids Alphabet Code Ciphers And Codes



Red Luth Riddle Tools
The Enigma machine was invented at the end of World War I and used by the German military from the 1930s onward to encrypt messages With trillions of possible combinations, its codes wereEnigma, first contacts From 1928 the German army Wehrmacht started to test a new cipher system This caused panic in the ranks of the Polish Secret Service After the end of the First World War France and Great Britain believed that Germany was no longer a threat to their security However, Poland never shared this opinion Solving the EnigmaInstead, every letter of the alphabet has been replaced by a number, the same number representing the same letter throughout the puzzle All you have to do is decide which letter is represented by which number!



Enigma Machine



The Enigma 1
The Enigma machine is a complicated apparatus consisting of a keyboard, a set of rotors, an alphabet ring, and plug connections, all configurable by the operator For the message to be both encrypted and decrypted, both operators had to know two sets of codes A daily base code, changed every 24 hours, was published monthly by the Germans This code simulates the Enigma machine, minus the plugboard Here's some test code that illustrates how the machine's construction and use (string) encipherings for the machine's alphabet offset (int) the starting position of the rotor """ def __init__(self, mappings, offset=0) selfinitial_offset = offset selfreset() selfforwardCryptiiText to Enigma Cryptiiv2 Cryptii Convert, encode, encrypt, decode and decrypt your content online Attention!



The Enigma Enigma How The Enigma Machine Worked Hackaday



Enigma And A Way To Its Decryption
Classic Ciphers In cryptography, a cipher (or cypher) is a method for protecting data through encryption and decryption Most ciphers require a specific key for encryption and decryption, but some ciphers like the ROT13 or Atbash ciphers have fixed keys Many of the ciphers listed here were for military or other significant use during anAll letters of the alphabet are used The Enigma code is set in a crossword format, each row or column will spell a word when completed correctly We have given you a starting either a letter or letters to get you started! Enigma allowed an operator to type in a message, then scramble it by means of three to five notched wheels, or rotors, which displayed different letters of the alphabet



Q Tbn And9gctaic9ualbu7t3hnrdub1qtagbjp5orkdfv3jigtfjmkl4xjs4x Usqp Cau




Enigma Rotor Details Wikipedia
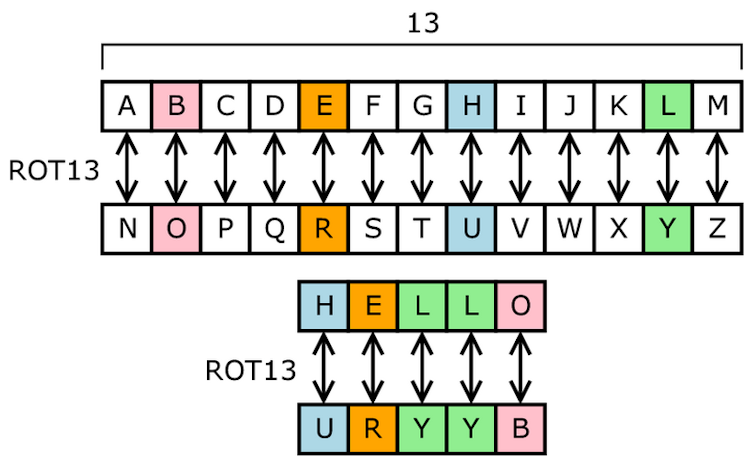
The name "Morse code" is misleading because, this is in fact a cipher not a code All the letters of the alphabet, number from 09 and some punctuation marks have been replaced by dots, dashes or short and long beeps For example A is " " The Enigma code was also broken by the Polish 4 PublicKey CrytographyThis meant that the same letter of the alphabet would be encoded to a different letter each time it was used in a message (If this weren't the case it would have been almost trivial to crack an Enigma message) Effectively each letter in a message was encoded using its own unique code It was this fact that made the Enigma so difficult to defeat The next step is to shift all the letters up the alphabet by one for each letter that we go up in the alphabet So, if we want ring setting C, we go up by 2 in the alphabet (Start out at A, B = 1;



Http Www Singingbanana Com Enigmaproject Maths Pdf




Enigma Codeproject
Alphabet The display windows at the top of Figure 1 show the letters JLY The three encoding is reversible also makes life easier for anyone trying to break the Enigma code Breaking the Enigma code Although you don't need it for the assignment, the decryption strategy first developed inExplore Tanya Coventry's board "Codes and puzzles" on See more ideas about alphabet symbols, alphabet, coding Getty Images In World War II, the Allies faced a dilemma The German Enigma machine created encrypted messages, and the Germans changed the code every day Even if a code



Red Luth Riddle Tools




Free Enigma Code Vector Art
Encryption with Caesar code is based on an alphabet shift (move of letters further in the alphabet), it is a monoalphabetic substitution cipher, ie a same letter is replaced with only one other (always the same for given cipher message) The most commonly used shift/offset is by 3 letters Enigma Machine ★ All Tools ★ This code dates back to the time of the Freemasons It is a geometric simple substitution cipher, which exchanges letters for symbols which are fragments of a grid The alphabet is coded in grids in 2 groups of 9 letters and 2 groups of 4 letters By using the outline of the box in which the letter is located you can write a real coded messageC = 2) Shifting up the alphabet means, an A becomes a B, a B a C, and so on




Substitution Cipher Png Images Pngwing



What Actually Was The German Enigma Machine What Was The Code That Needed To Be Cracked And What Messages Did They Actually Send Quora
The Code Book The Science of Secrecy from Ancient Egypt to Quatum Cryptography Fourt Estate Limited, London 1999 11 Gordon Welchman The Hut 6 Story Breaking the Enigma Codes M&M Baldwin 05 (originally 1997) 12 B Jack Copeland (Editor) The Essential Turing The ideas that gave birth to the computer age Clarendon Press, OxfordEnigma Enigma was a ciphering (code communication) system used by the German military from 1926 until the end of World War II, and by several other nations for some years after Enigma was the first mechanized messageencryption system to see wide use Enigma produced such thoroughly scrambled messages that for many years its cipher was 25 June 21 Codewords are like crossword puzzles but have no clues!




Home Make Diy Projects And Ideas For Makers Enigma Machine Ciphers And Codes Enigma



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher
The Enigma rotor cipher machine was potentially an excellent system It generated a polyalphabetic substitution cipher, with a period before repetition of the substitution alphabet that was much longer than any message, or set of messages, sent with the same keyTo start you off, we reveal the codes for two or three letters2 The Enigma Machine 2 21 Encryption and Decryption Process 3 22 Enigma Weaknesses 4 221 Encrypting the Key Twice 4 222 Cillies 5 223 The Enigma Machine Itself 5 3 Zygalski Sheets 6 31 Using Zygalski Sheets 6 32 Programmatic Replication 7 33 Weaknesses/Problems 7 4 The Bombe 8 41 The Bombe In Code 10 411 Making Menus 10




Codes And Ciphers Puts Students To Test Bryn Mawr Alumnae Bulletin




Enigma Machine Brilliant Math Science Wiki
The Enigma machine created a different cipher alphabet for every consecutive letter of plaintext Two important characteristics were the result of the socalled reflector, which we will look at in more detail later (1) the alphabet was reciprocal and (2) a letter could never be encoded as itself The Enigma machine is a cipher device developed and used in the early to midth century to protect commercial, diplomatic, and military communication It was employed extensively by Nazi Germany during World War II, in all branches of the German militaryThe Germans believed, erroneously, that use of the Enigma machine enabled them to communicateEnigma decoder Decrypt and translate enigma online The Enigma cipher machine is well known for the vital role it played during WWII Alan Turing and his attempts to crack the Enigma machine code changed history Nevertheless, many messages could not be decrypted until today Bitwise calculator Text to base64
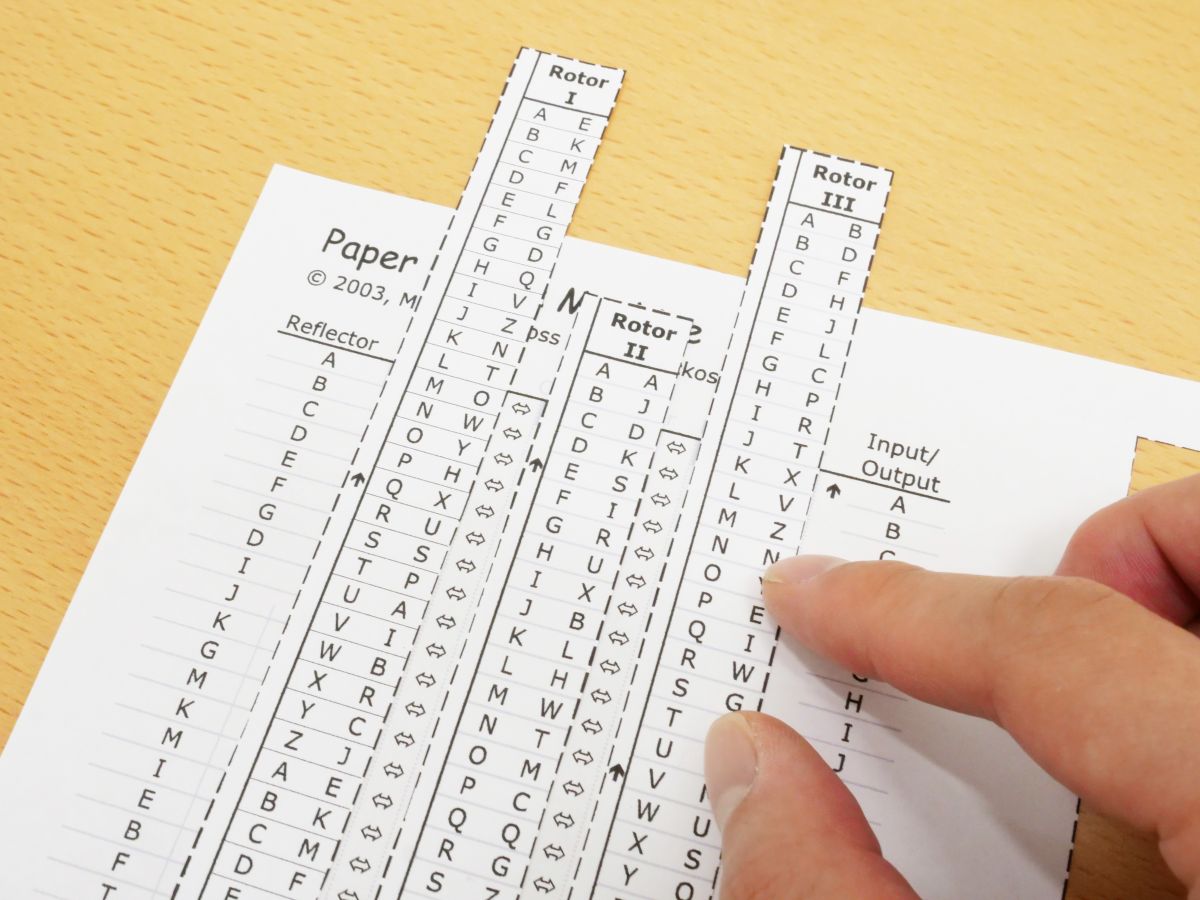



I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine




Enigma Codeproject
This version of cryptii is no longer under active development Find the latest version on cryptiicom Cryptii is an OpenSource web application under the MIT license where you can encode and decode between different format Another enigma that surrounds the Polish alphabet are the phantom letters Q, V and X They're not in the language, but they show up from time to time and this confuses me V, for instance, isn't in the written language, but does exist in body language – I've seen many Poles holding up two fingers to show the V for victory gestureAn enigma style simulation machine in Python 3 This code made a few breaks back in my spare time There are, however, a few alterations to the original machine that this simulation shows, one being the alphabet, another being the amount of rotors If you happen to run this you'd find this to be slow (please run in console, not shell)




The Human Errors That Defeated Enigma Openmind



Cryptography How Much Time It Would Take To Decode Enigma Code Machine If Modern Computers Were Available Quora



Enigma Procedure




Secret Codes For Writing Codes And Ciphers Ciphers And Codes Encrypted Messages Coding




Pin On Cryptography



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher



The Polish Attack On Enimga
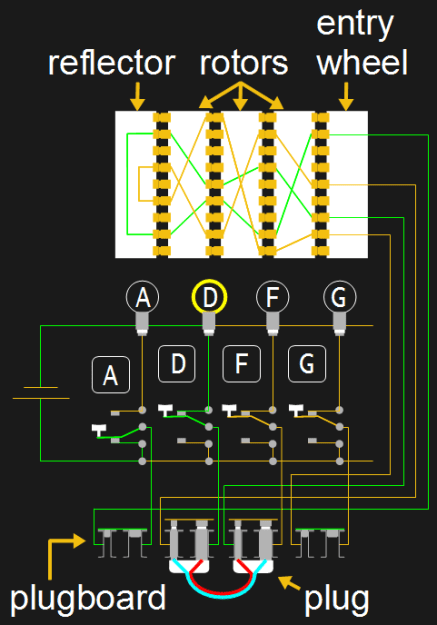



The Enigma Enigma How The Enigma Machine Worked Hackaday



Red Luth Riddle Tools




I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine




Polyalphabetic Cipher Wikipedia




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium



Q Tbn And9gcrjt7fe0q Rbajjaws1tmrkmopoqgujiemyxudtj4xnlwiqcovd Usqp Cau



Enigma Procedure
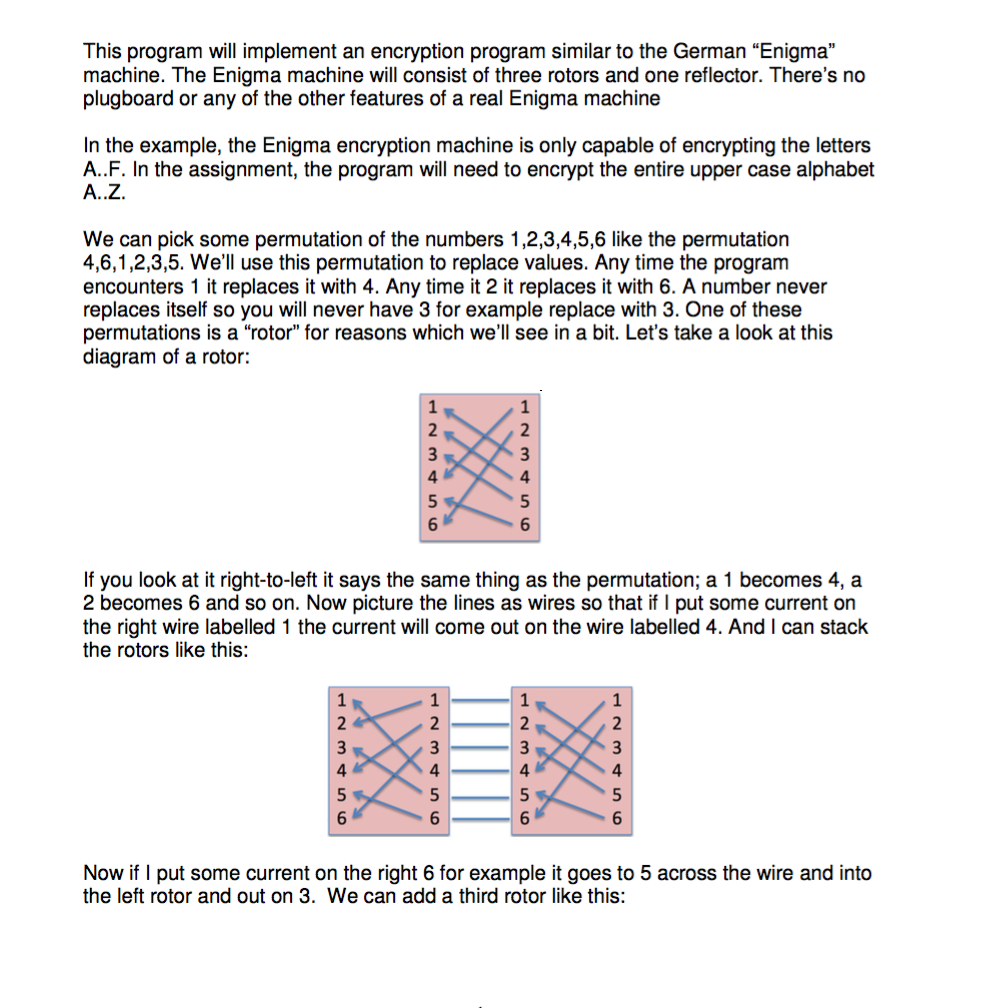



This Program Will Implement An Encryption Program Chegg Com




The Enigma Cipher Machine And Breaking The Enigma Code
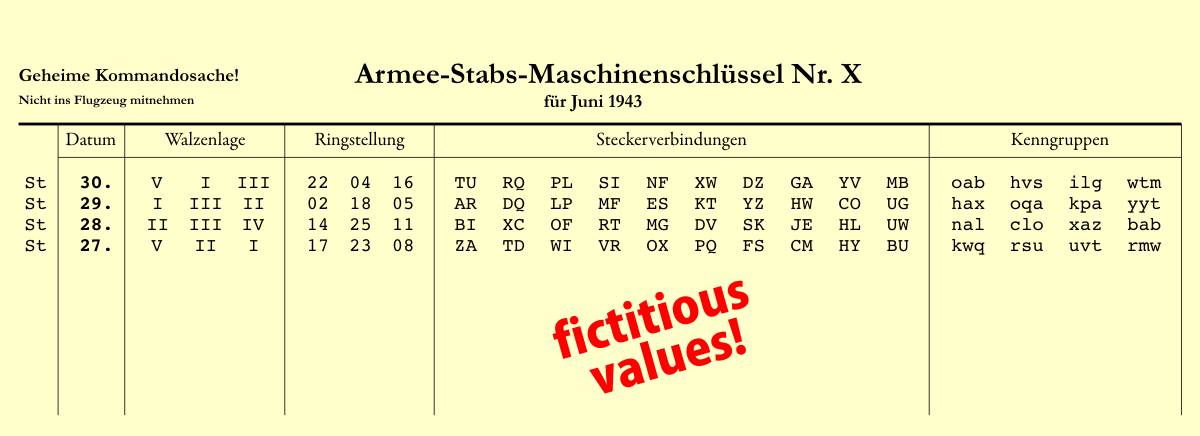



Enigma The German Cipher Machine




Project 1 Enigma




Enigma 37 Encryption Machine With Letters Numbers Encode And Etsy



Enigma




Enigma Simulator Bitsf463 Assignment 1 Question Contests Hackerrank




How Did The Enigma Machine Work Computing The Guardian



Enigma The German Cipher Machine



Enigma Machine By 101computing Net



Description Of The Enigma




Enigma Machine Brilliant Math Science Wiki




Lets Talk About Ciphers



1



Cryptology I Vigenere Based Systems



2




The Enigma 1




The Enigma 1




The Human Errors That Defeated Enigma Openmind




The Enigma Cipher Machine And Breaking The Enigma Code




Cryptanalysis Of The Enigma Wikipedia



1




Linear Algebra In Cryptography The Enigma Machine



The Polish Attack On Enimga




The Enigma Machine Tony Sale



Enigma Procedure




Charlesreid1




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium




1 2 3 Code Cycle 3 Activities Lesson 3 4 How To Ensure A Message Is Secure Le Site De La Fondation La Main A La Pate




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium



Project 1 Cs 61b Spring



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher




Enigma Technology And The History Of Computers




Rotor Machine Wikiwand



The Human Errors That Defeated Enigma Openmind




Enigma Key Book Photo From Authentic German Codebook From Before Download Scientific Diagram



Codebreaking Has Moved On Since Turing S Day With Dangerous Implications




Ic211 Oop And Enigma
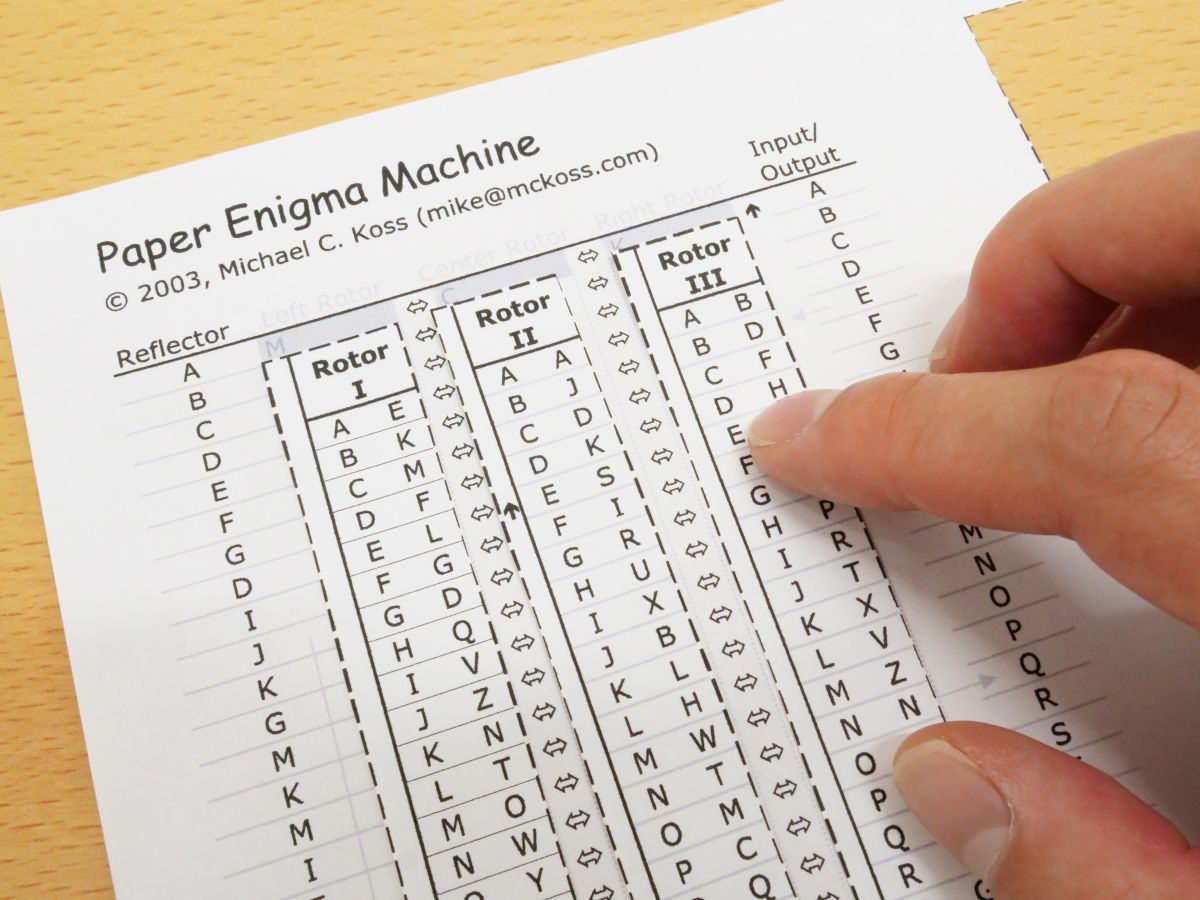



I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine




Enigma Machine Wikipedia
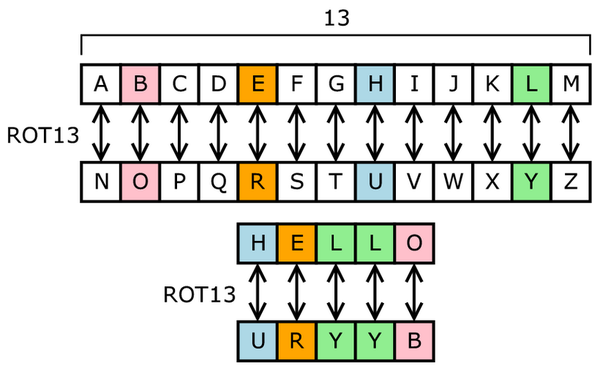



Substitution Cipher Wikiwand
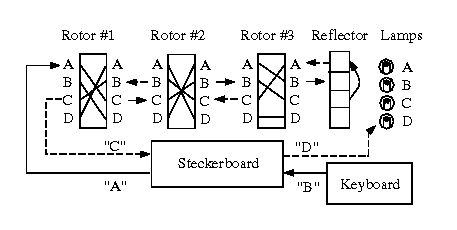



Cryptology I Vigenere Based Systems




How To Build An Enigma Machine Virtualisation In Python By Vasile Păpăluță Analytics Vidhya Medium




How The Enigma Works Nova Pbs



Enigma Cipher




Codes And Ciphers Puts Students To Test Bryn Mawr Alumnae Bulletin



Enigma
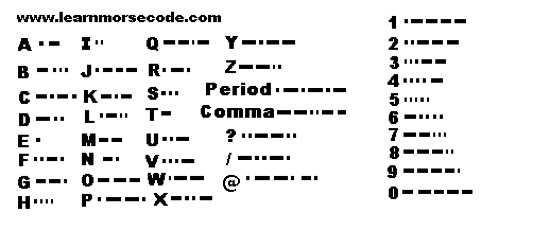



Top 10 Codes And Ciphers Listverse




The Enigma Cipher Machine And Breaking The Enigma Code
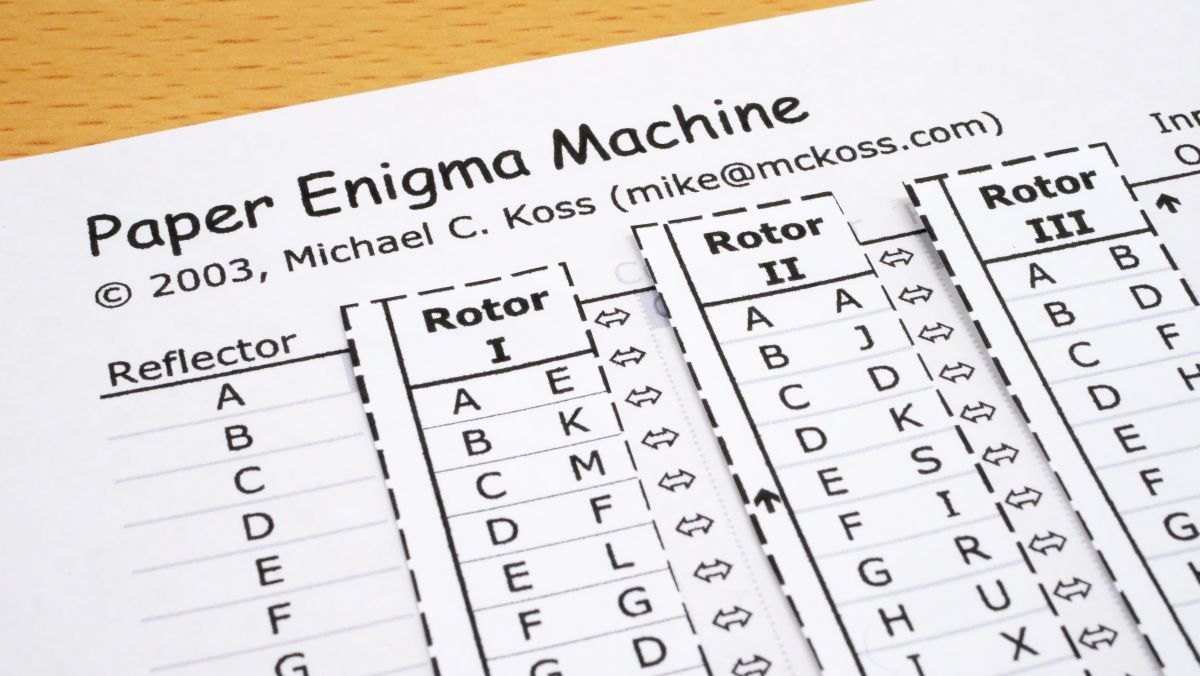



I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine



The Enigma Machine And The Ultra Secret South African Military History Society




Bletchley Park Enigma




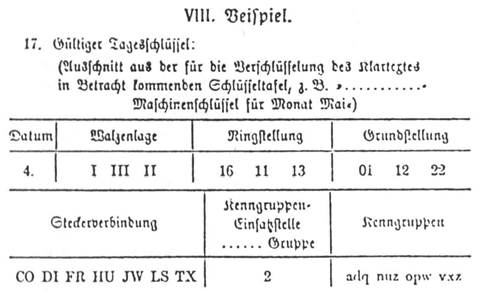
Enigma Daily Settings Generator 101 Computing



Investigations Enigma



Exploring The Enigma Plus Maths Org




Hobo Signs Richard Gallon We Are Here



The Polish Attack On Enimga
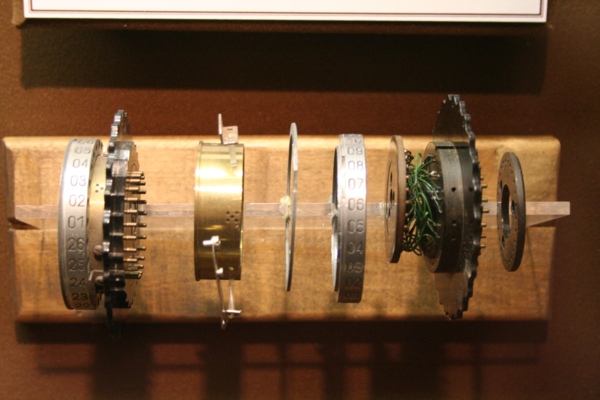



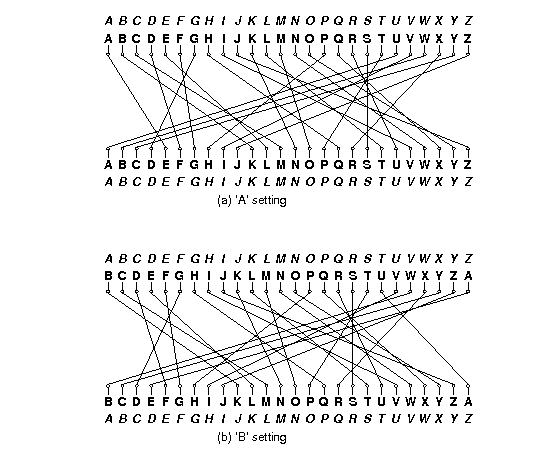
Enigma Rotor Details Wikipedia




Virtual Caesar Cipher Wheel Program The Invent With Python Blog Caesar Cipher Cipher Wheel Secret Alphabet



Web Stanford Edu Class Cs106j Assignments Assignment 05 Cryptography Pdf




Universal Turing Machine Wikipedia




Enigma 1349 Alphabet Magic Enigmatic Code



0 件のコメント:
コメントを投稿